Pure Web3 Outline
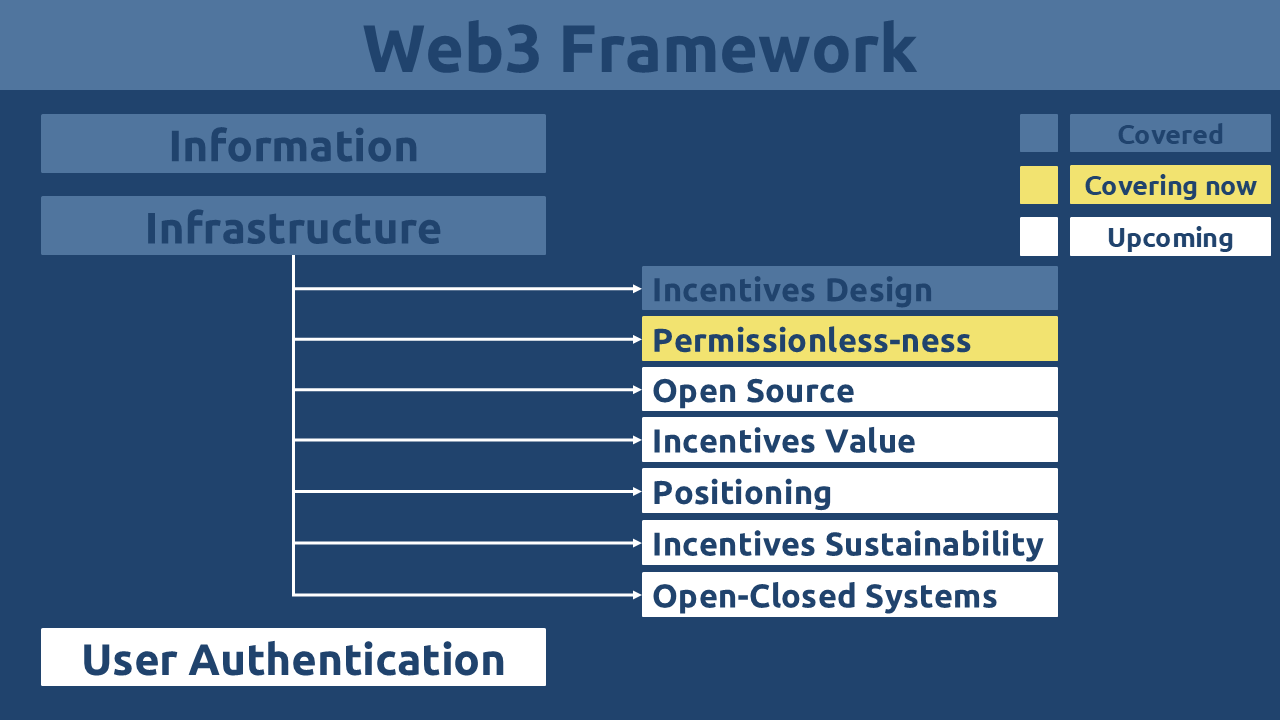
The Pure Web3 sub-series will be released in multiple parts for easier comprehension. The following figure outlines the series’ structure, showing which sections are already covered, currently being covered, and coming soon.
Permissionless-ness
The core principle of permissionless validation asks a fundamental question: can anyone participate? This concept breaks down into two critical dimensions:
- Protocol-Level Permissionless-ness: Does the network’s code explicitly allow any user to run a validator?
- Practical Permissionless-ness: If the protocol allows it, what are the real-world barriers to entry, and how difficult are they to overcome?
Radical Inclusivity
In reality, even the most open blockchain networks fall short of being radically inclusive. Universal participation is impossible due to three fundamental, global prerequisites for running a validator node:
- Reliable Electricity: Access to a stable and continuous power supply.
- Reliable Internet: A consistent and robust internet connection.
- Sufficient Capital: The financial means to acquire the necessary hardware or the minimum stake required.
While these may seem like basic requirements readily available across developed nations, they remain significant and often insurmountable obstacles in many parts of the world, creating an inherent limit to true inclusivity.
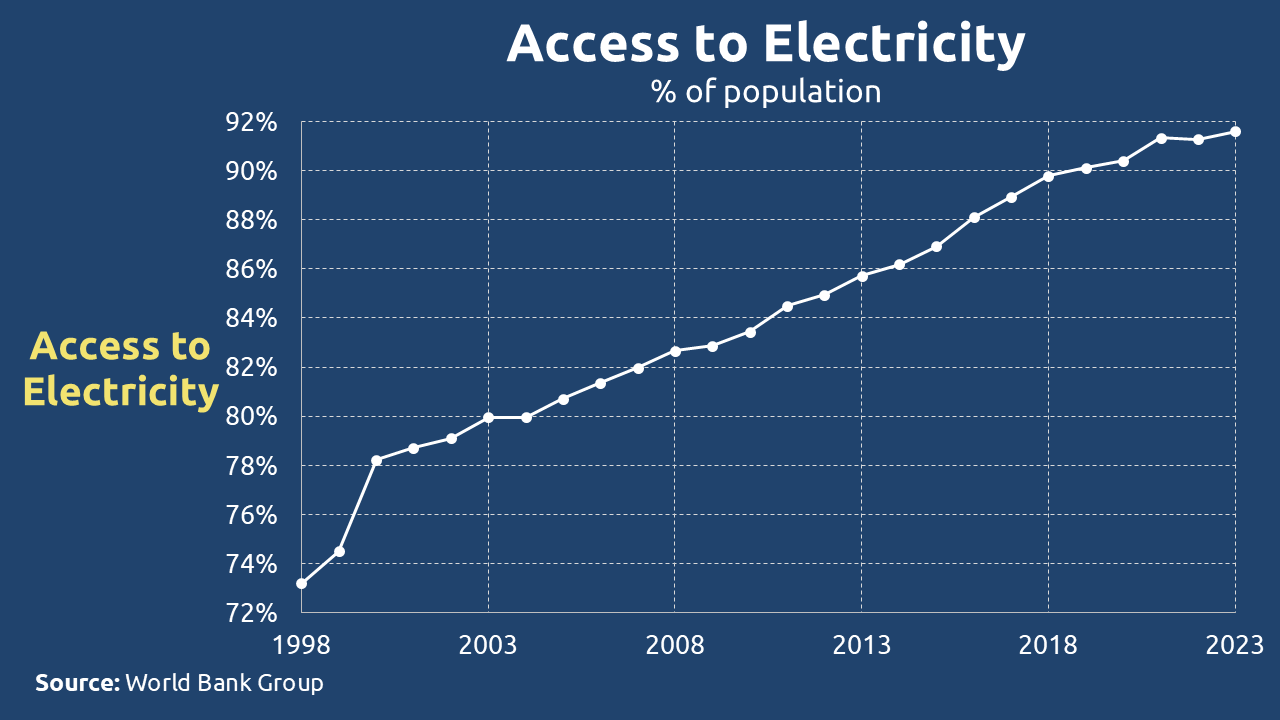
The data reveals a significant gap between theoretical access and practical reality. For instance, while a reported 92% of the global population has access to an electricity source, this statistic often masks critical issues of stability, consistency, and capacity. Frequent outages or insufficient wattage can render a validator node inoperable, effectively barring participation.
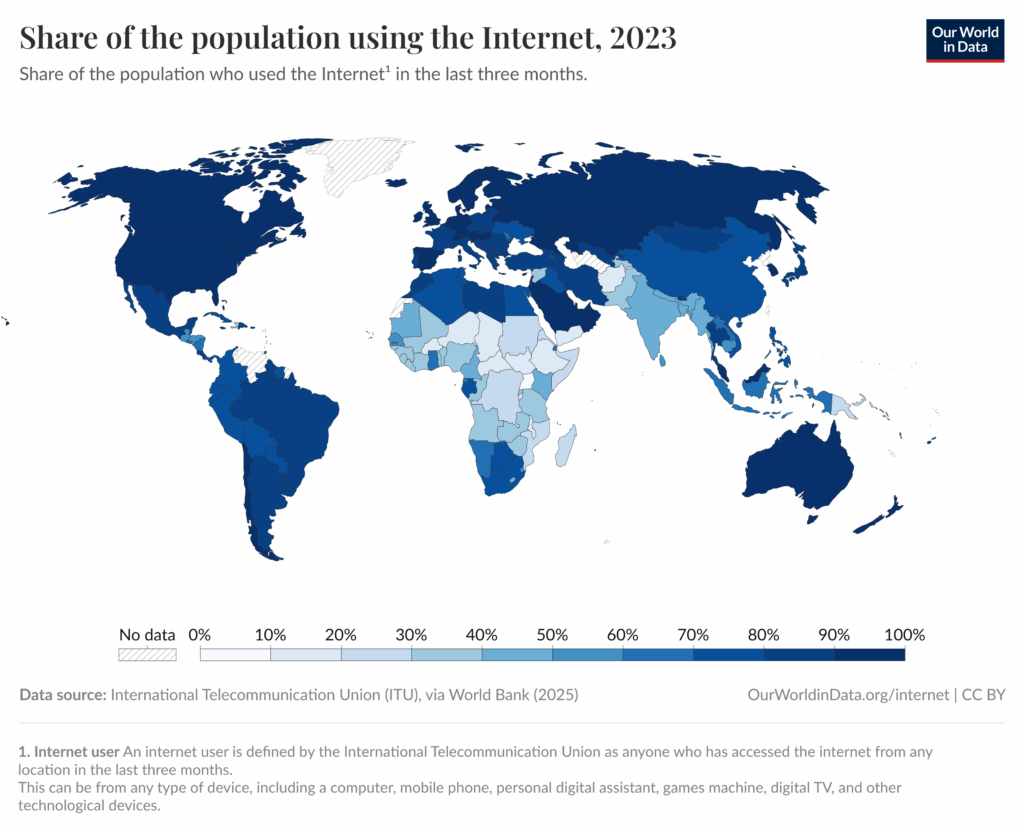
The situation is even more stark with internet connectivity. As of 2023, only approximately 63% of the world’s population was online according to Our World in Data. Furthermore, mere connectivity does not guarantee the high bandwidth, low latency, or uncapped data required for a node to reliably stay in sync with a blockchain network.
The barrier of hardware cost exacerbates this problem. Global income inequality means that a computer considered basic or outdated in a developed nation remains an unaffordable luxury for vast segments of the world’s population.
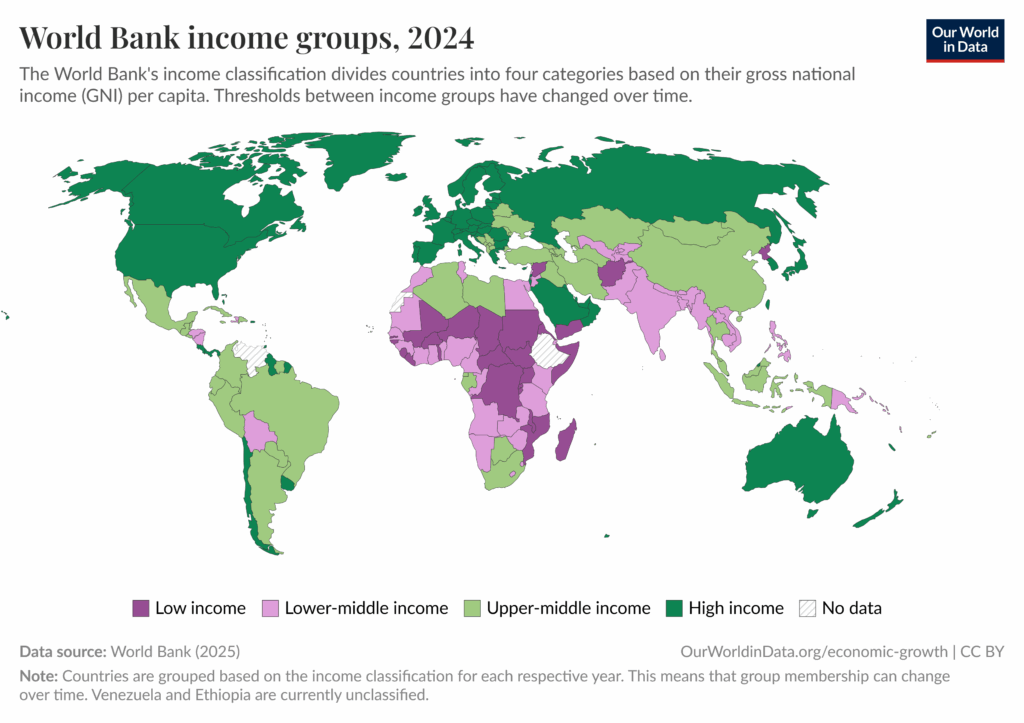
The World Bank’s income classifications, based on Gross National Income (GNI) per capita in 2024, highlight this stark economic divide:
- Low-income economies: ≤ $1,135
- Lower-middle-income economies: $1,136 – $4,495
- Upper-middle-income economies: $4,496 – $13,935
- High-income economies: ≥ $13,936
Given that radical inclusivity is unattainable, a blockchain genuinely committed to permissionless participation would strive to minimize its protocol-level barriers, making validation accessible to everyone who can meet these basic global prerequisites.
Unfortunately, the prevailing trend moves in the opposite direction. Many protocols intentionally design excessively high hardware or staking requirements at the protocol level, creating a system that is theoretically permissionless but practically permissioned. This contradiction is often masked by marketing rhetoric from venture capital backers who promote values like inclusivity and fairness.
When a protocol’s design choices make validation unfeasible for the vast majority of people – even in wealthy nations – while its promoters speak of “decentralization” and “creating parallel infrastructures,” a clear deception is at play. Their actions reveal their true priorities. The following analysis will examine this discrepancy in detail across different blockchain architectures.
PoW Blockchains
In contrast to many popularly marketed protocols, most Proof-of-Work (PoW) blockchains like Bitcoin, Litecoin, Dogecoin, and Monero uphold a fundamental principle: any user can genuinely become a validator.
It is crucial to note that while permissionless access is not an inherent requirement of all PoW systems, it is a defining feature of its most famous and successful implementations.
The hardware requirements for basic participation are kept intentionally minimal. This low barrier to entry allows anyone with a simple machine to download the client software and begin participating in the network’s consensus and validation processes, truly embodying the permissionless ideal.
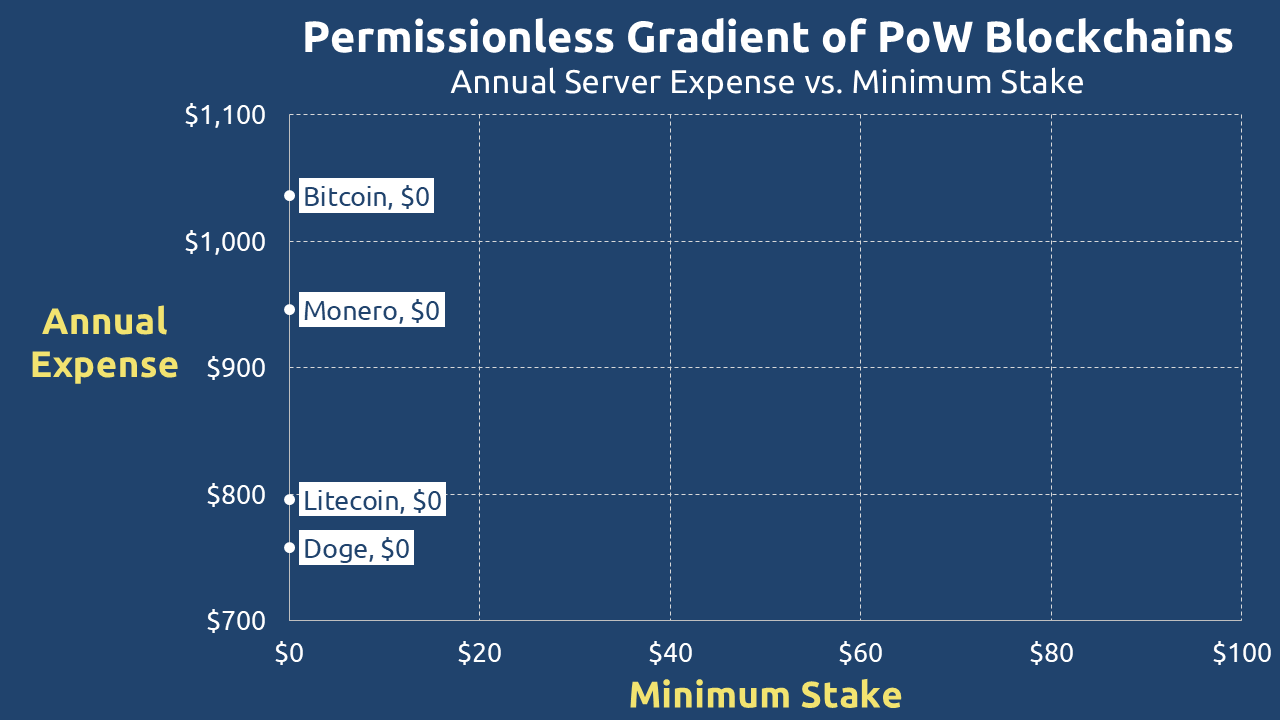
To provide a consistent comparison, Figure 4 details the approximate annualized cost of running nodes for major PoW chains based on Google Cloud server pricing, highlighting their relative affordability.
A common point of confusion arises from the intense competition in networks like Bitcoin, visualized by its skyrocketing total hash rate.
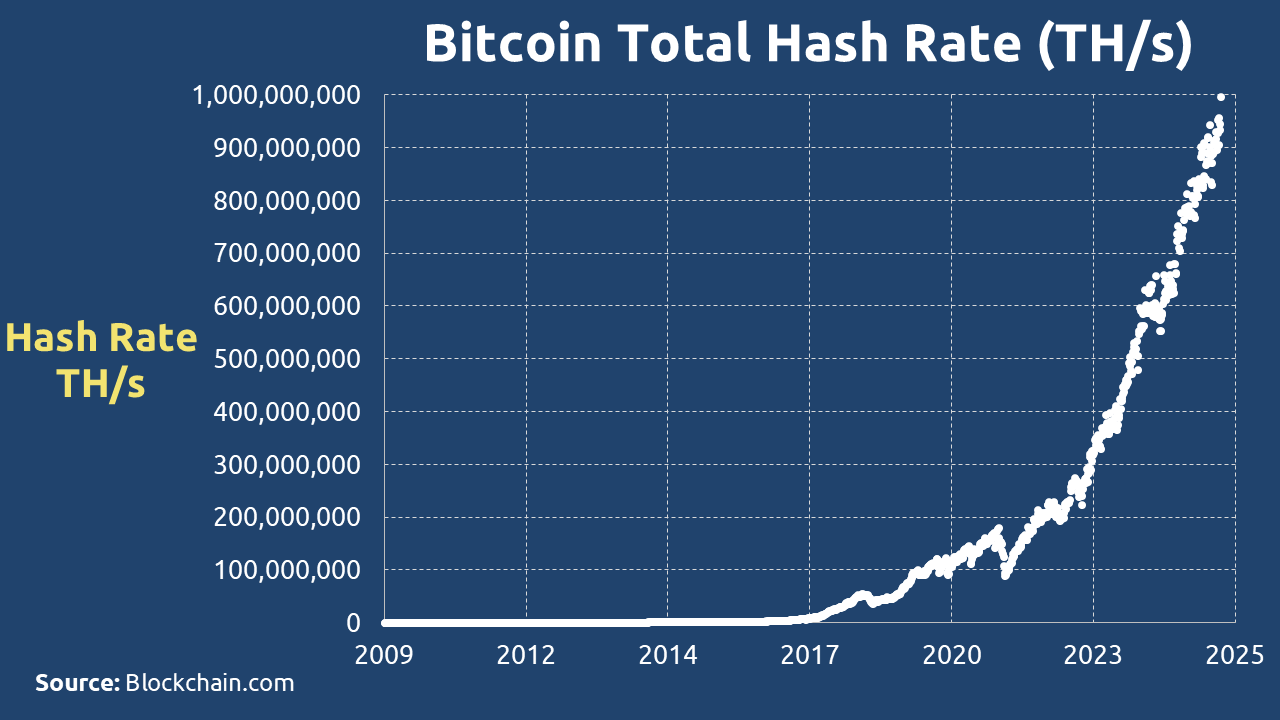
Proponents of more restrictive systems often point to this competitive landscape to justify their own high barriers to entry. However, this argument deliberately conflates two very different concepts:
- The minimum requirement to participate: The basic hardware needed to run the client software and validate the chain.
- The requirement to compete profitably: The advanced hardware needed to have a statistically significant chance of earning block rewards.
This is a critical distinction. The PoW protocol itself does not discriminate against users with basic hardware. While a machine with minimal specs (e.g., 1 GB RAM, 1 CPU core) has a near-zero chance of successfully mining a block in today’s competitive environment, it is still allowed to participate. It can still fully validate transactions and maintain the ledger’s history. The opportunity – however slim – to earn rewards remains open to all, and the network’s security benefits from every additional node, regardless of its hash power. The protocol’s design ensures that the door to participation is never officially closed, preserving its core permissionless nature.
PoS Blockchains
This is where the narrative often diverges from reality. Many Proof-of-Stake (PoS) blockchains have introduced staggering hardware and staking requirements that fundamentally alter the permissionless promise. These protocols frequently defend their “permissionless” label by focusing on a narrow technicality: the absence of a central party to whitelist validators. However, they conveniently ignore the immense economic and technical barriers they erect.
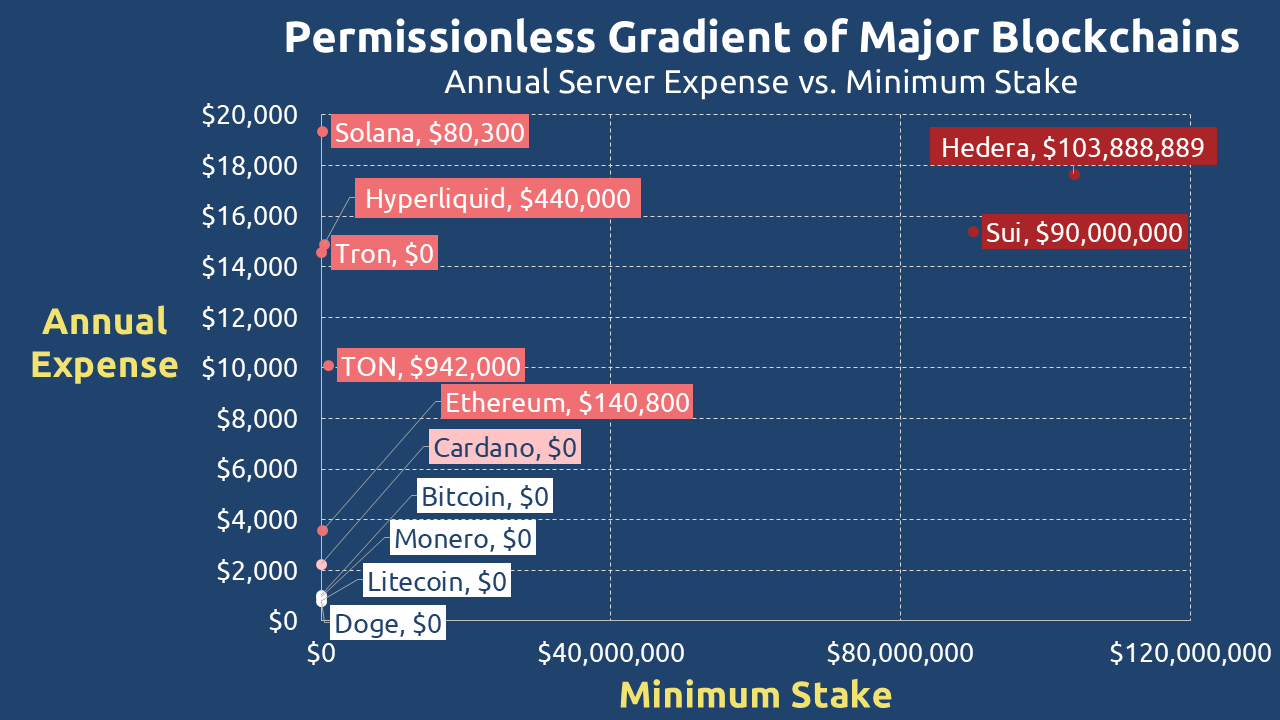
The data in Figures 6 and Figure 7, compiled from official protocol sources, paints a clear picture. One could charitably interpret the rationale behind these prohibitive costs as a twisted form of pragmatism: if perfect inclusivity is already impossible due to global inequalities in electricity and internet access, why not prioritize performance and further limit the validator set?
This logic is profoundly flawed. The original ethos of Web3 was to empower average individuals and create a resilient alternative to centralized government and corporate control. By designing systems accessible only to high-net-worth individuals or institutional entities, these PoS blockchains are merely recreating the exclusive, hierarchical structures of Web2. This raises a critical question: if the goal is centralization, aren’t existing Web2 monopolies, with their established efficiency and scale, simply better than their inefficient “Web2.5” counterparts?
The stark contrast between theoretical permissionless-ness and practical exclusion is undeniable in the data:
| Type | Blockchain | Memory (In GB) | Core | Disk Space (In GB) | Annual Expense | Min Protocol Stake |
| PoW | Bitcoin | 1 | 1 | 350 | $1,036 | N/A |
| Doge | 2 | 1 | 60 | $758 | N/A | |
| Monero | 2 | 1 | 100 | $796 | N/A | |
| Litecoin | 2 | 2 | 256 | $946 | N/A | |
| PoS | Ethereum | 16 | 4 | 2000 | $3,580 | $140,800 |
| Cardano | 24 | 2 | 250 | $2,256 | $0 | |
| Tron | 64 | 32 | 3500 | $14,568 | $0 | |
| Sui | 128 | 24 | 4000 | $15,390 | $90,000,000 | |
| Hyperliquid | 128 | 32 | 1000 | $14,907 | $440,000 | |
| TON | 128 | 16 | 1000 | $10,113 | $942,000 | |
| Solana | 256 | 12 | 2000 | $19,354 | $80,300 | |
| Hedera | 256 | 24 | 240 | $17,665 | $103,888,889 |
Figure 7. Recommended Requirements to Run a Validator Node | Sep 2025
Do not be misled. The principle is simple: do not trust – verify. When a protocol claims to be permissionless but simultaneously enforces insurmountable protocol-native costs for participation, it is being deliberately deceptive. This is not decentralization; it is a carefully designed illusion of it.
Private Blockchains
In contrast to the often-misleading claims of public PoS networks, private blockchains are explicitly and intentionally permissioned. Participation as a validator is restricted to a pre-approved, exclusive list of entities, typically enterprise insiders or specific consortium members. By design, no external user can ever join this validator set.
This closed model raises a fundamental question regarding adoption: why use a blockchain at all? Legacy Enterprise Resource Planning (ERP) and centralized database systems are often more efficient for private business operations. The alleged benefits of “trustless-ness” and “immutability” become questionable in a system where a small group of known validators has full control over the ledger. Without the ability for outsiders to verify or participate, these properties are not inherent to the system but are instead promises made by the controlling members, fundamentally undermining the core value proposition of blockchain technology.
FBA Blockchains
As noted earlier, networks like XRP (utilizing Federated Byzantine Agreement) present a complex case. They claim a degree of permissionless-ness by allowing any user to run a validator node. However, this permissionless-ness is superficial.
The critical flaw in this model is the requirement for users to adopt a nearly identical Unique Node List (UNL) to achieve consensus and avoid network forks. This practice effectively centralizes trust around a small, curated set of authorized validators. While anyone may theoretically run a node, the protocol’s design inherently discourages meaningful participation beyond the pre-approved entities. Without a tangible economic incentive or a real role in consensus, there is little reason for users to operate validators outside of specific, non-critical use cases, reinforcing the system’s de facto permissioned nature.
DApps
While many decentralized applications (DApps) successfully maintain permissionless access, significant exceptions exist.
Applications like Uniswap V2 exemplify the permissionless ideal: users can participate as liquidity providers without minimum investment thresholds, identity verification (KYC), or approval processes. This creates a truly open financial system where global access is limited only by one’s willingness to engage.
However, this openness is not universal across the ecosystem. For example, in many crucial infrastructure projects access remains heavily restricted and often requires explicit permissions, creating centralized points of failure in otherwise decentralized networks.
A clear example of this permissioned infrastructure is Axelar. To become a validator, candidates must undergo a vetting process managed directly by the Axelar corporate stakeholders, including a detailed validator questionnaire hosted by Google Forms (Figure 8). This approach – backed by $144 million in venture funding – creates a gatekept system where the team ultimately controls who can participate. In practice, this eliminates any possibility of permissionless access for average validators.
This centralized model is common among major bridges. The Wormhole bridge, which suffered a $320 million exploit in 2022, is secured by just 19 pre-selected “world’s top validator companies”, effectively excluding independent or community validators.
Similarly, the Ronin Bridge – which lost $600 million in another 2022 exploit – limits block production to only 22 validators. Among these, 12 Governing Validators include Enterprises like Google and DappRadar DAO, raising serious questions about how decentralized its “community-elected” model truly is.
Despite their claims of decentralization, these bridges function as permissioned systems, placing critical cross-chain infrastructure under the control of a small number of entities. This not contradicts the ethos of Web3 but also introduces significant security risks, as highlighted by their histories of major exploits.
The Illusion of Permissionless-ness
As illustrated in Figure 9, there exists a critical distinction between theoretical protocol design and practical accessibility. While many blockchain projects including Hyperliquid, Solana, XRP, Ton, and Sui publicly champion their permissionless nature, their actual validator requirements reveal a different reality.
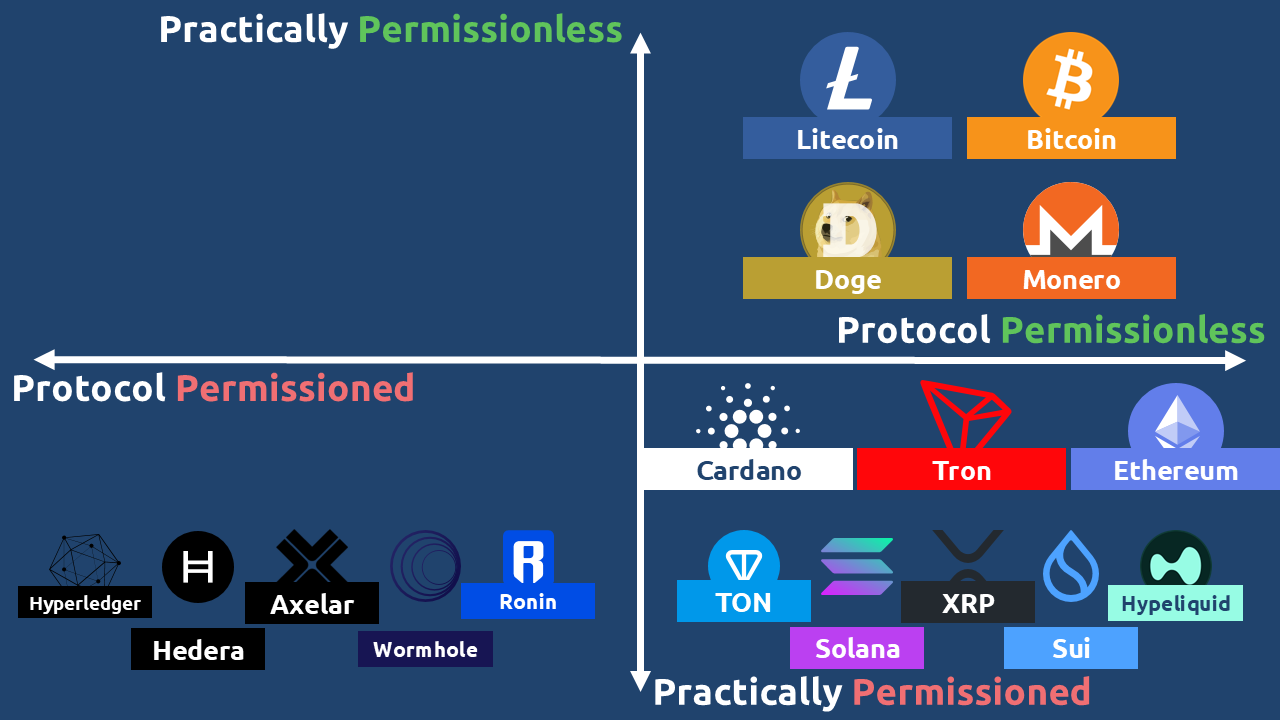
A protocol that cannot run on consumer-grade hardware has effectively established a permissioned system. When node operation demands enterprise-level machines, specialized data centers, or prohibitively expensive staking requirements, the system excludes the average participant regardless of its theoretical openness. Such projects are more accurately described as practically permissioned. They maintain the appearance of decentralization while functionally operating under institutional-grade barriers.
This contradiction represents one of the most significant unacknowledged issues in blockchain today: protocols that claim to be decentralized while designing systems only large entities can realistically operate. True permissionless-ness requires not just protocol-level openness, but also practical accessibility. Truly permissionless blockchains must enable broad participation rather than reinforcing the very centralized structures blockchain technology aimed to disrupt.
Faking Permissionless-ness
Many projects often promote an illusion of decentralization by emphasizing validator count – claiming 19, 21, or even 75 nodes as evidence of a robust, permissionless system. Yet, the number of nodes alone is a misleading metric. A network with 1,000 nodes hosted exclusively on Google Cloud remains functionally centralized – it is controlled by a single corporate entity. Similarly, when investment elites spread capital across multiple validator operations under the same umbrella organization, they create an illusion of decentralization while retaining consolidated control.
Web3’s original appeal lay in its capacity to enable any individual to participate as a validator. Web3’s promise is to create an alternative economic system that diffuses power rather than reinforcing existing hierarchies. Unfortunately, many contemporary Web2.5 projects exploit the average user’s limited technical insight, using the language of permissionless-ness to mask what are, in practice, highly gatekept and centralized systems.
Permissioned = Centralized
When protocols impose extreme hardware specifications, unaffordable staking thresholds, or enterprise-level infrastructure demands, they effectively exclude everyday users. In such systems, nodes inevitably migrate to data centers like AWS or Google Cloud, creating single points of technical, legal, and economic control.
Worse still, the reliance on corporate hosting and traditional payment systems introduces further centralization. Validators must inevitably undergo Know Your Customer (KYC) procedures via credit card payments and identity-linked VPS accounts. Essentially, running a node entail eroding the anonymity and censorship resistance that define true Web3 values.
What emerges is a system that is permissioned not by protocol, but by practice – a modern form of digital enclosure disguised as innovation. If participation is limited to entities that can meet corporate-scale technical, financial, and identity requirements, the resulting network is absolutely centralized. It is simply a less efficient version of the legacy systems it claims to replace.