Pure Web3 Outline
The Pure Web3 sub-series will be released in multiple parts for easier comprehension. The following figure outlines the series’ structure, showing which sections are already covered, currently being covered, and coming soon.
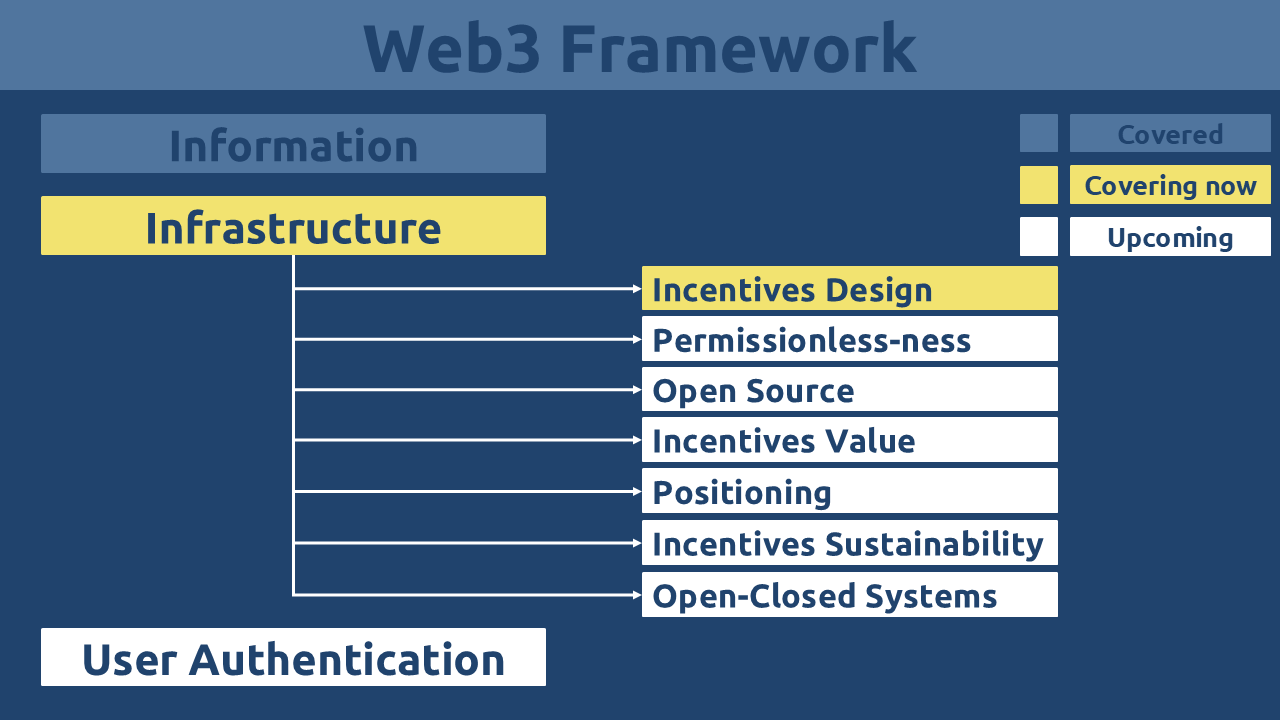
Infrastructure
Web1 infrastructure was distributed. Individuals and organizations independently hosted static pages on their own servers. This model was simple to maintain but limited in functionality, offering little beyond basic information sharing.
Web2 emerged in response to growing demand for user interaction. Yet, as Murphy’s Law aptly observes, “every solution breeds new problems.” Supporting real-time, user-generated content required vastly more complex server architectures capable of handling immense loads and enabling dynamic engagement. This complexity led to inevitable centralization, as only well-resourced corporations could build and maintain the necessary infrastructure. In turn, this centralization brought familiar consequences: pervasive data collection, mandatory user authentication, and platform-controlled governance.
Web3 represents a fundamental shift leveraging unified data standards to decentralize infrastructure through distributed networks of validators. Rather than relying on centralized servers, Web3 protocols use consensus mechanisms to maintain a shared ledger across countless independent nodes. This approach combines the resilience and openness of Web1 with the interactivity of Web2 but without the central points of control or failure.
The long-term operability of any Web3 network is not a given; it depends entirely on validators’ ongoing commitment to maintaining its infrastructure. Consequently, an ecosystem’s validity as a true Web3 platform can be measured by analyzing the specific economic and technical parameters that determine whether a rational validator would choose to support it.
Incentives Design
Effective incentive structures are the cornerstone of sustainable blockchain systems. At the base layer, validators must be economically motivated to act honestly and penalized for malicious behavior.
PoW Blockchains
Proof-of-Work (PoW) model exemplifies this principle. Miners are rewarded with native coin rewards (e.g. BTC) for confirming legitimate transactions but incur significant energy expenses if they attempt to subvert the network.
PoS Blockchains
Proof-of-Stake (PoS) operates on a comparable incentive structure: validators who follow the protocol rules are rewarded with the network’s native cryptocurrency, while those who act maliciously or fail to perform their duties risk having a portion (or all) of their staked assets permanently seized.
Private Blockchains
Private distributed ledgers such as Hyperledger operate without built-in cryptoeconomic incentives, which is a fundamental limitation that has restricted their real-world adoption and utility. Unlike public blockchains that reward honest validation and penalize malicious behavior, private blockchains rely entirely on off-chain reputational pressure. Participants are motivated only by the need to maintain operational integrity and avoid organizational scandal, as misconduct could lead enterprises to abandon the platform.
This model introduces critical vulnerabilities. With a small, pre-approved validator set and no financial stakes – block rewards and slashing – the network remains exposed to collusion, coercion, and apathy. The absence of programmable incentives and the reliance on trusted rather than trustless verification place Hyperledger and similar frameworks squarely outside the realm of decentralized innovation. It is precisely this architectural shortcoming that has confined such systems to limited enterprise applications and prevented mass adoption.
FBA Blockchains
Networks utilizing Federated Byzantine Agreement (FBA), such as XRP, amplify the fundamental limitations of permissioned systems like Hyperledger. While Hyperledger operated without a native cryptocurrency – making its closed, enterprise-centric nature transparent – XRP introduces a publicly traded token that creates a deceptive impression of decentralization and financial opportunity.
Unlike other public blockchains (e.g. PoW, PoS) that reward validation or penalize misbehavior, XRP provides no protocol-level incentives for running a node. There are no staking yields, no transaction fee rewards, and no slashing mechanisms to deter malicious actors. The only potential gains are speculative, based on secondary market token price movements – a benefit unrelated to the actual work of validation.
Consequently, operating a validator is economically irrational unless the participant is an enterprise with off-chain vested interests in the network, such as a financial institution or liquidity provider. This absence of embedded incentives severely restricts node operation to a small group of large, known entities, fundamentally undermining any claim to meaningful decentralization. The system functionally operates as a permissioned consortium masked by the illusion of an open token-based economy.
Retail Users
The statement by the CTO of XRP that “the best incentive is no incentive” underscores a foundational design choice: validator participation is intended to be driven not by financial rewards, but by operational need. This means that the entities running validator nodes are typically institutions – exchanges, payment providers, or enterprise – whose core functions depend on the real-time integrity and accuracy of the XRP Ledger. For these organizations, operating a node is a practical measure to independently monitor transaction validity and scrutinize the conduct of other validators on their Unique Node List (UNL).
A defining and deliberate feature of this system is the intentional stability of the UNL. The list is designed to be highly static, consisting of a limited number of large, well-established, and publicly accountable organizations.
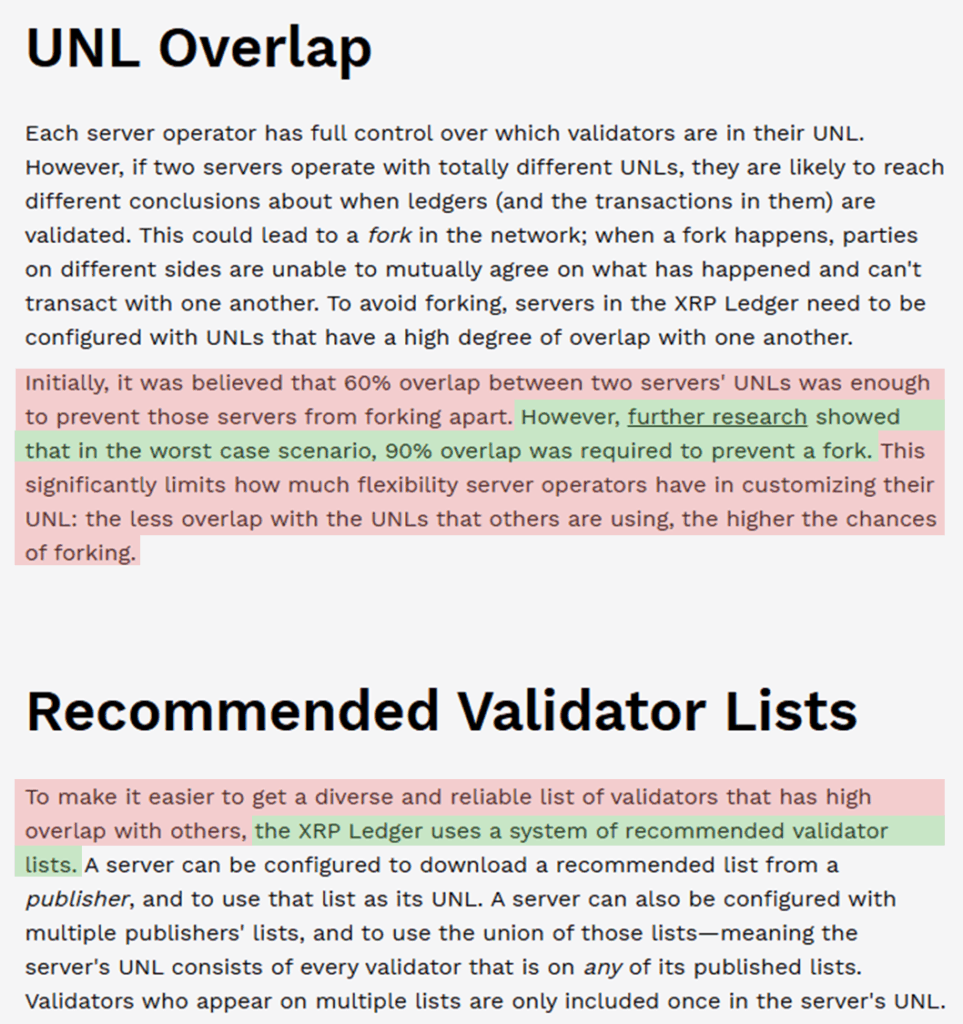
This low variability is not a side effect but a core requirement. The security model depends heavily on the reliability and reputation of these known entities, rather than on a dynamic, open, or permissionless set of validators. The trusted status and predictable behavior of UNL participants are meant to replace the need for on-chain incentives or penalties.
For regular users, even those with significant XRP holdings, there is no meaningful incentive and no meaningful agency to run a validator. An individual cannot influence the consensus process or counteract malicious actions orchestrated by the dominant institutions on the UNL. If validators were to collude in censoring transactions or altering balances, a user-operated node could detect this – but it could not prevent it. The system offers no protocol-level recourse, leaving users dependent on the very institutions they might need to challenge.
In essence, the XRP Ledger substitutes cryptographic and economic security with a model based on institutional trust and static membership. This makes it reliable for certain enterprise use cases but places it in direct opposition to the permissionless, incentive-driven, and crypto economically secured models that characterize genuinely decentralized networks.
The single greatest risk to any user on such a network is transaction censorship. Specifically, the possibility that validators will collectively blacklist your address by refusing to include user’s transactions in their mempools or by dropping them before they can be confirmed.
Enterprise
For an enterprise, the incentive to run a validator is primarily defensive: to independently monitor the network and guard against potential malicious actions by other participants. This setup creates a critical game-theoretic dilemma rooted in the highly static and centralized nature of the Unique Node List (UNL).
Since the UNL is composed of a fixed set of large, known institutions, an enterprise must constantly assess the trustworthiness of this exclusive group. It must ask: which of these powerful actors could conspire against us? To defend itself, the enterprise would need to hold a stake in XRP so large that an attack on them would be economically irrational for the conspiring validators – i.e., the attackers’ losses from the resulting market collapse would have to exceed the enterprise’s own losses.
However, this defense is fundamentally flawed for several reasons:
- Asymmetry of Power: An individual enterprise is almost always “outgunned” by the collective stake and influence of the established UNL members. The system is designed to be stable, not democratic, concentrating power in a fixed roster of elites.
- The Exit Problem: Even if malicious activity is detected and proven, the attackers – being large, sophisticated players – would likely liquidate their positions before making their move or before the victim can publicize the attack. They would profit from their actions and exit before the news triggers a market-wide sell-off that would punish later holders.
- No On-Chain Recourse: The protocol itself offers no slashing mechanism or cryptographic punishment. The only consequences are off-chain: reputational damage and potential legal action. However, no validator operates under a contract that legally binds them to protocol security, making lawsuits complex and uncertain.
- Reliance on Web2 Systems: This model completely depends on traditional, centralized systems for enforcement: Centralized Exchanges (CEXs) for liquidity and price discovery, and courts for legal recourse. This is the antithesis of a trustless, decentralized blockchain, as it reverts to the very institutions Web3 aims to circumvent.
The composition of the UNL – intentionally non-variable and comprised of “notorious” organizations – creates an environment where the “elites” (existing validators) can easily coordinate to their mutual benefit at the expense of outsiders or the general public. Rather than designing protocol-level incentives to ensure good behavior, the system relies on external forces to manage internal failures, making it more of an openly centralized, court-dependent system than a closed, crypto economically secure one.
This raises a final, critical question: if retail participants are actively disincentivized from joining the network as validators, who exactly are the “players”? The ecosystem is effectively a game for a small consortium of large institutions and the core team, which notably controls nearly half of the total XRP supply. This concentration of ownership and influence invites further scrutiny: what forms of malicious activity might be occurring on-ledger but remain unchallenged because the same entities that would police the network are also the ones who potentially benefit from its lapses?
DApps
For a Decentralized App (DApp) to be truly decentralized and sustainable, its design must incorporate clear mechanisms for both rewards and penalties. This principle applies at the smart contract level, where logic should be immutable and non-upgradable, ensuring that administrative roles cannot alter core functions or tokenomics without broad consensus. In DAO-governed DApps, similar incentive structures must enforce accountability among participants.
A prime example of effective decentralized design is Uniswap V2. Its contracts are largely immutable, and the protocol lacks significant administrative control. Instead of traditional validators, liquidity providers (LPs) act as economic participants—earning fees from trading activity while bearing market risk through impermanent loss. This creates a natural incentive alignment without relying on centralized intervention.
In contrast, most cross-chain bridges exhibit poorly designed or ambiguous incentive structures. Facilitating interoperability between chains requires robust infrastructure, yet many bridge designs fail to meaningfully reward honest behavior or penalize malicious activity. A critical flaw in many systems is the retention of upgradability in bridge contracts, which introduces centralization risk.
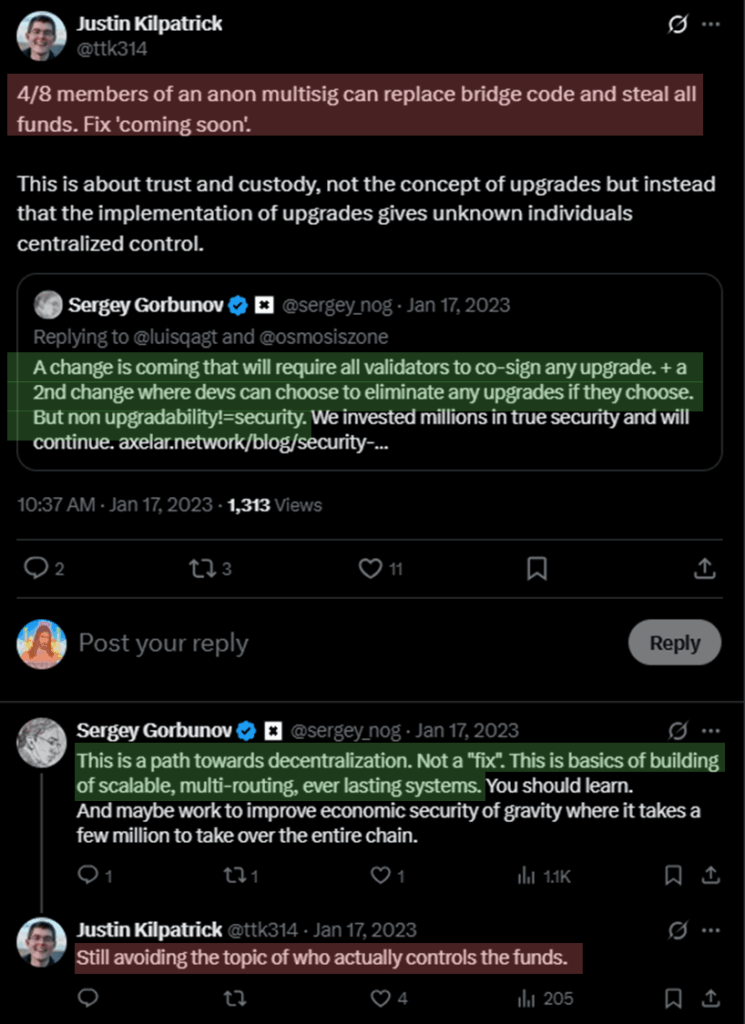
For instance, the Axelar bridge maintains upgradable smart contracts, raising serious concerns about who controls upgrade permissions and what accountability exists for harmful changes. Crucially, validators within the Axelar network have no definitive authority over these upgrades – a responsibility held by a separate multi-signature wallet, as evidenced by the AxelarGatewayProxyMultisig contract. This separation of power contradicts the ethos of validator-governed security and places ultimate control in the hands of a non-validator entity.
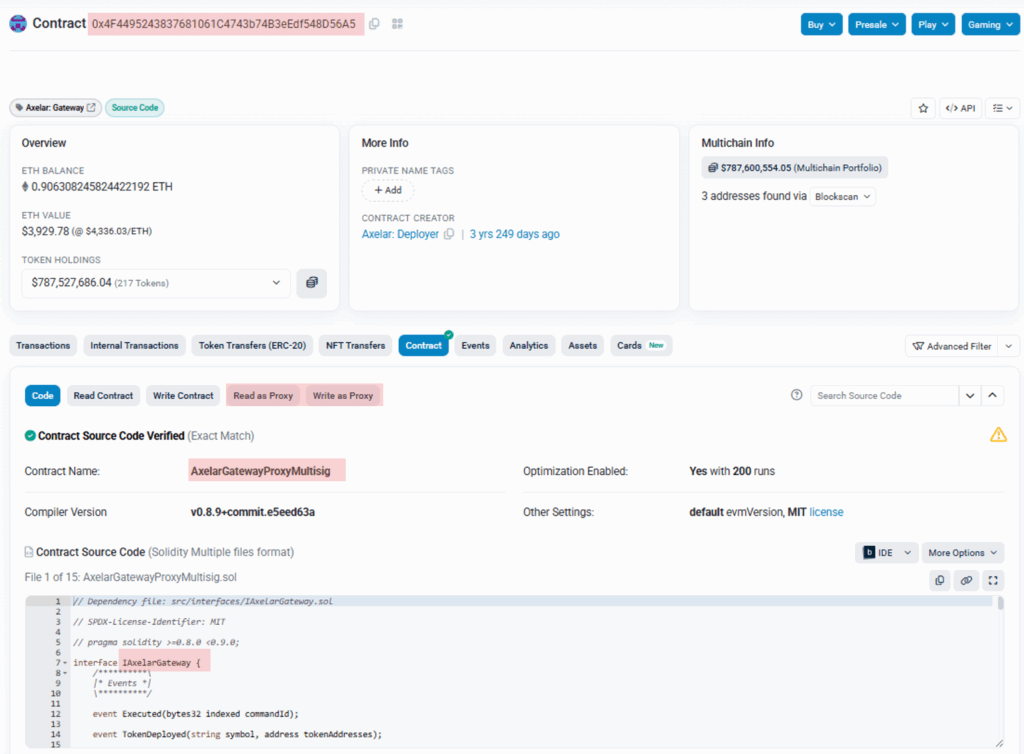
Of course, the Axelar Gateway smart contract, which facilitates cross-chain connectivity with Ethereum, remains fully functional and retains upgradeable administrative privileges.



