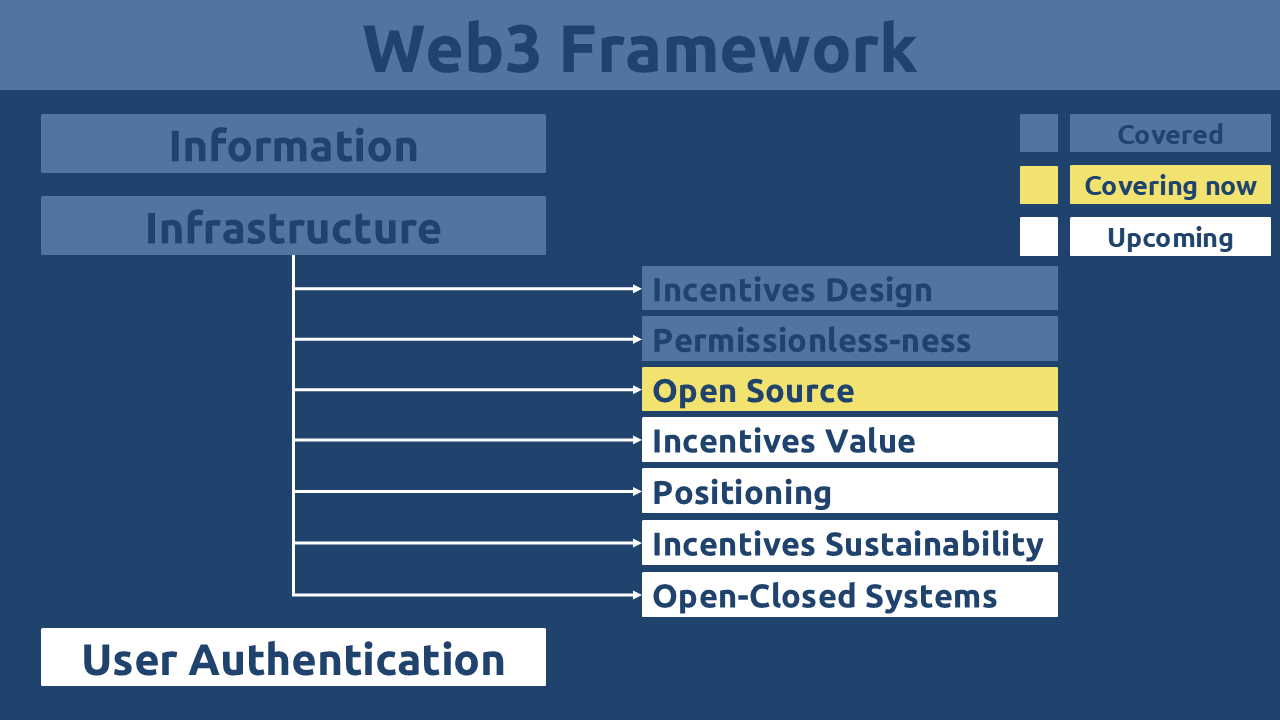
Pure Web3 Outline
The Pure Web3 sub-series will be released in multiple parts for easier comprehension. The following figure outlines the series’ structure, showing which sections are already covered, currently being covered, and coming soon.
Open-Source
Open-source code is non-negotiable in Web3 – it is a core requirement and the de facto standard. This commitment to transparency fundamentally distinguishes Web3 from the proprietary, closed-source nature of Web2.
This openness is a natural extension of the permissionless principles explored earlier: true accessibility requires not only the ability to participate but also the ability to verify, modify, and redeploy the underlying technology.
Fortunately, the majority of Web3 projects uphold this standard, releasing their code under recognized open-source licenses that permit use, review, reuse, and redistribution. Such practices enable trustless-ness, collaboration, and iterative innovation across the ecosystem.
Scientific Citations Analogy
In academic research, the impact of a publication is measured by how often it is cited. The more references it attracts, the greater its influence and credibility. Similarly, in open-source development, the success and reliability of a codebase are reflected in how frequently it is adopted, forked, and built upon. This cycle of reuse and reference is not merely imitation. It is how meaningful technological progress is achieved. Just as citations advance science, open collaboration and code sharing propel innovation in Web3.
Bitcoin Forks
As the founding public blockchain, Bitcoin’s influence extends far beyond its own network. It has directly inspired a long lineage of forks and derivatives: from direct codebase splits like Bitcoin Cash, Bitcoin SV, and Bitcoin Gold, to spiritually indebted projects like Litecoin, Dogecoin, and Zcash.
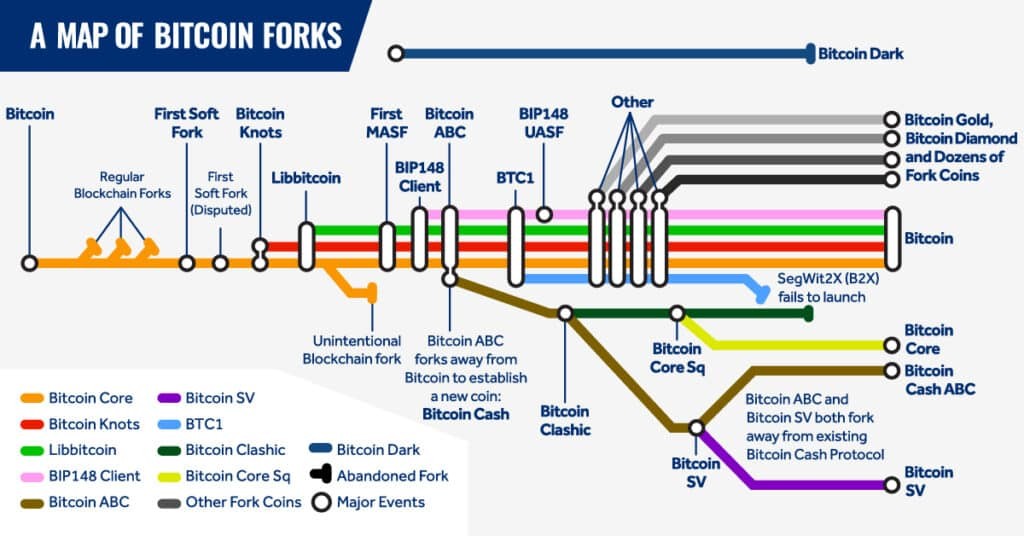
What made this proliferation possible and truly revolutionary was Satoshi Nakamoto’s decision to release Bitcoin’s code as open source. At the time, many questioned why such groundbreaking technology would be given away freely.
The answer was foundational to Web3’s ethos: trustless-ness through transparency.
By open-sourcing the code, Satoshi enabled anyone to verify how the software worked, ensuring there were no hidden functions, backdoors, or risks of double-spending or malware. Miners and users could run the node with confidence, knowing exactly what they were participating in. This openness didn’t weaken Bitcoin. It became its greatest strength, enabling auditability, innovation, and global participation without permission.
EVM forks
One of Ethereum’s most significant contributions was the creation of the Ethereum Virtual Machine (EVM), the runtime environment that executes smart contracts and powers the decentralized logic the network is known for.
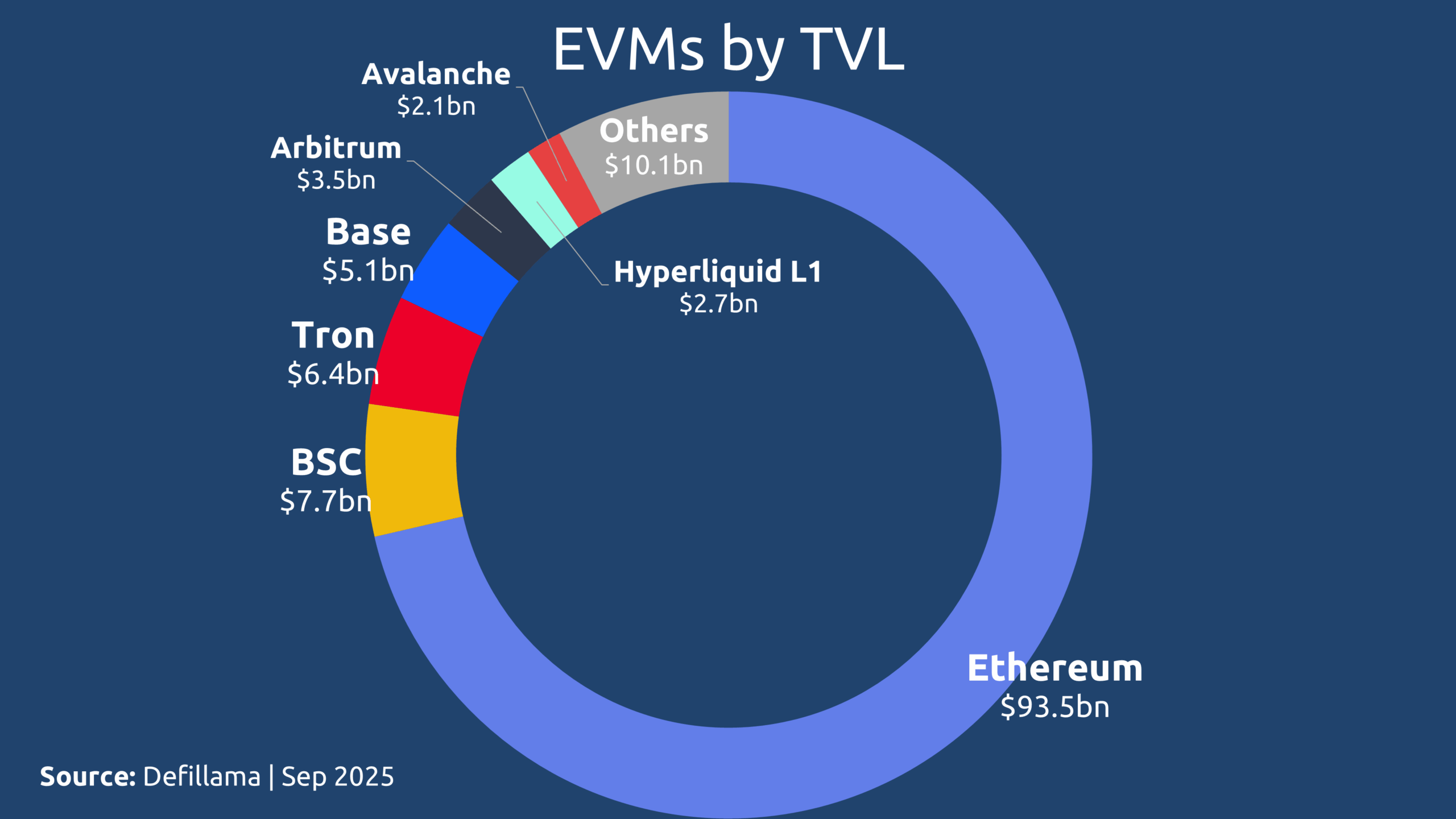
Because the EVM was open-sourced, it did not just stay within Ethereum. It became a shared public good that launched countless compatible chains. Early adopters like Binance Smart Chain (BSC), Tron, Polygon, and Avalanche built upon the EVM, while newer entrants like Base and Hyperliquid continue to leverage its open design.
Such EVM-compatibility has enabled projects such as ghostNFT to deploy seamlessly across 20+ EVM-compatible chains, demonstrating how open standards foster innovation, reduce fragmentation, and create a composable, interconnected ecosystem. The EVM didn’t just scale Ethereum. It scaled the entire idea of programmable blockchains.
Solana forks?
Blockchains like Solana, XRP, and SUI have gained significant market traction and developer attention. Yet we see almost no forks of these networks. Why are there no notable Solana forks? No NEAR forks? No Cardano forks? Even Polkadot, despite its modular Substrate framework, has inspired parachains rather than direct forks.
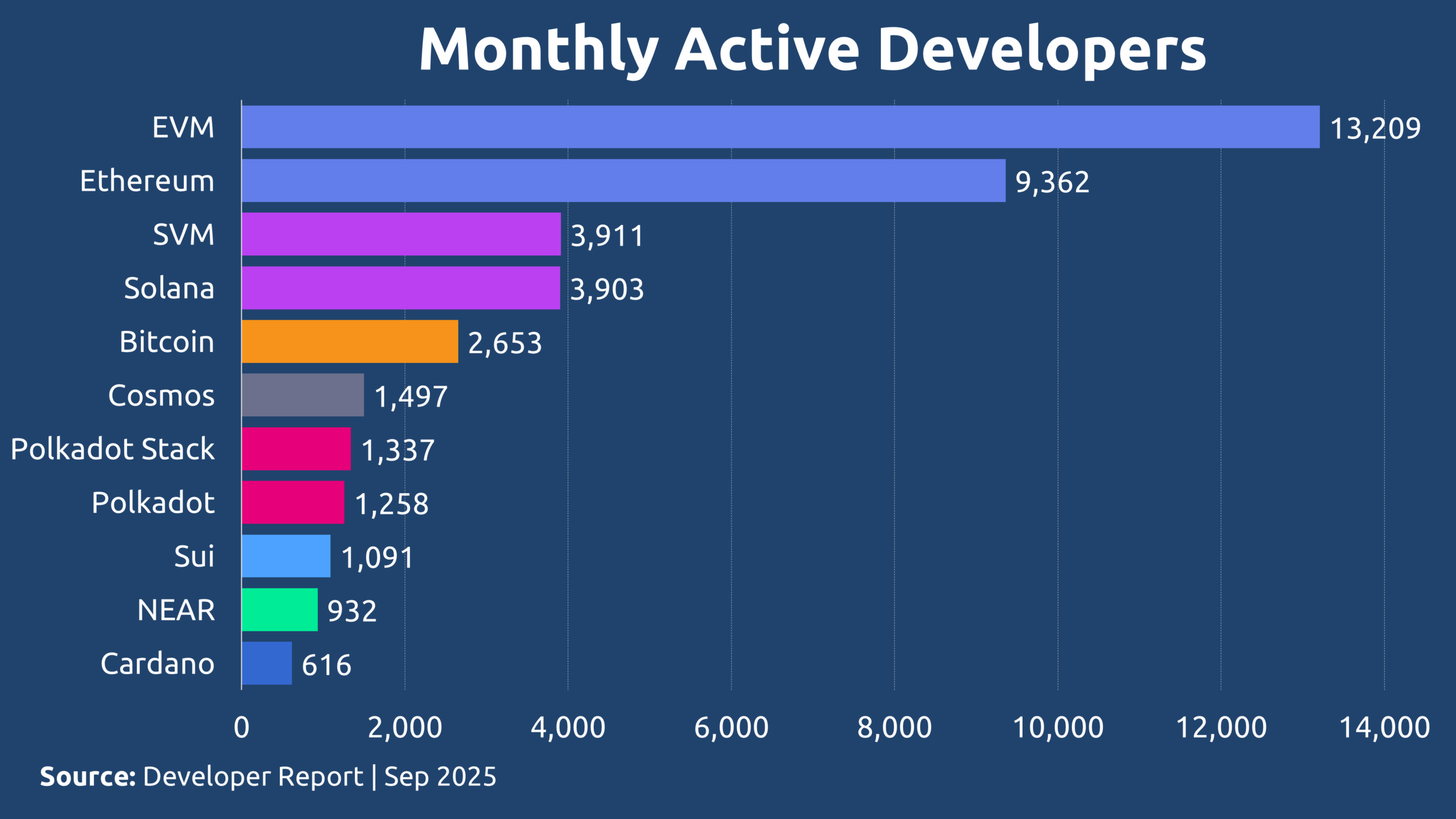
The answer lies in the deep relationship between open-source ethos and practical permissionless-ness. While many of these projects are open source in name, their runtime requirements and architectural choices make them effectively permissioned for operators.
It is far easier to design a system that demands higher resources than it is to simplify one for broader access.
For instance, an Ethereum light node can run on modest hardware (4GB RAM, 2 cores). Yet, as the following comparison reveals, nearly every major EVM-compatible chain imposes significantly higher demands:
| Chain | RAM | Cores | Storage |
| Ethereum | 4GB | 2 | 2TB |
| Optimism | 16GB | N/A | 2TB |
| Arbitrum | 16GB | 4 | N/A |
| Gnosis | 16GB | 4 | 1TB |
| Linea | 16GB | 4 | 1TB |
| Avalanche | 16GB | 8 | 1TB |
| Tron | 16GB | 8 | 3TB |
| Sonic/Fantom | 32GB | 4 | 1TB |
| Pulse | 32GB | 8 | 3TB |
| Polygon | 32GB | 8 | 4TB |
| Binance | 32GB | 16 | 2TB |
Figure 4. Minimum Node Requirements Per EVM.
These requirements are for minimum specs. Recommended setups are even higher. This creates a high barrier to entry, limiting who can run nodes and effectively centralizing infrastructure among those with capital and data-center resources.
Now consider Solana: its validator requirements are far beyond these at 256GB RAM, 12+ cores, and 2TB+ storage. This isn’t a chain you fork and run in a basement or a home lab. This is infrastructure only institutions and highly resourced individuals can realistically operate.
It is always easier to make a network more permissioned than more permissionless. You cannot easily “un-add” high hardware requirements or simplify deeply complex code. Once a chain is designed around high barriers, it stays that way and so, it attracts no forks.
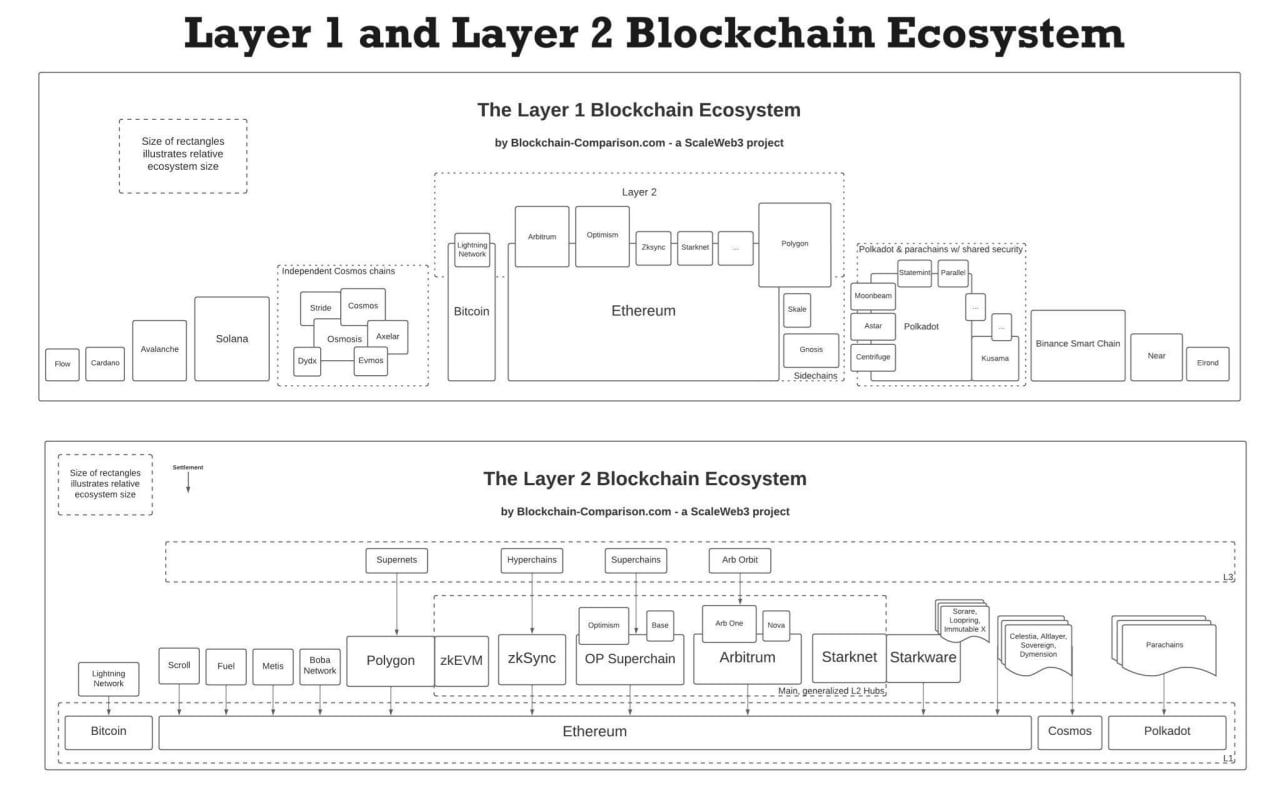
Fork = Innovation?
This raises a critical question: Did projects like Avalanche, Polygon, and Binance truly innovate or did they simply clone the EVM and inflate throughput by raising hardware requirements? While many EVM forks may not have introduced fundamental technical innovation, they undeniably spurred significant economic and developmental activity within the Web3 ecosystem. Not without strings attached in a form of heavy VC influence, but still.
Non-forked chains such as Solana, TON, and Sui became isolated islands. Their “lonely” ecosystems forced them to rely on centralized exchanges for liquidity and connectivity. When integration depends on CEX listings rather than technical interoperability, speculation dominates utility, and technology takes a back seat to price action.
This is one of the reasons how Web3 became polluted with Web2.5 hybrids.
Closed Source is the Future?
A troubling trend is emerging: many venture-backed projects are increasingly abandoning the open-source foundation of Web3, choosing instead to lock down their code. While this might offer short-term competitive advantage, it is a long-term strategic failure and a fundamental betrayal of Web3’s core values.
Let’s look at Hyperliquid. Despite its permissionless slogans, its core validator code is closed-source. The network’s 24 bridge validators are required to stake 10,000 HYPE (roughly $500,000 as of Sep 2025) yet have no visibility into the software they are running since it is delivered only via opaque Docker containers.
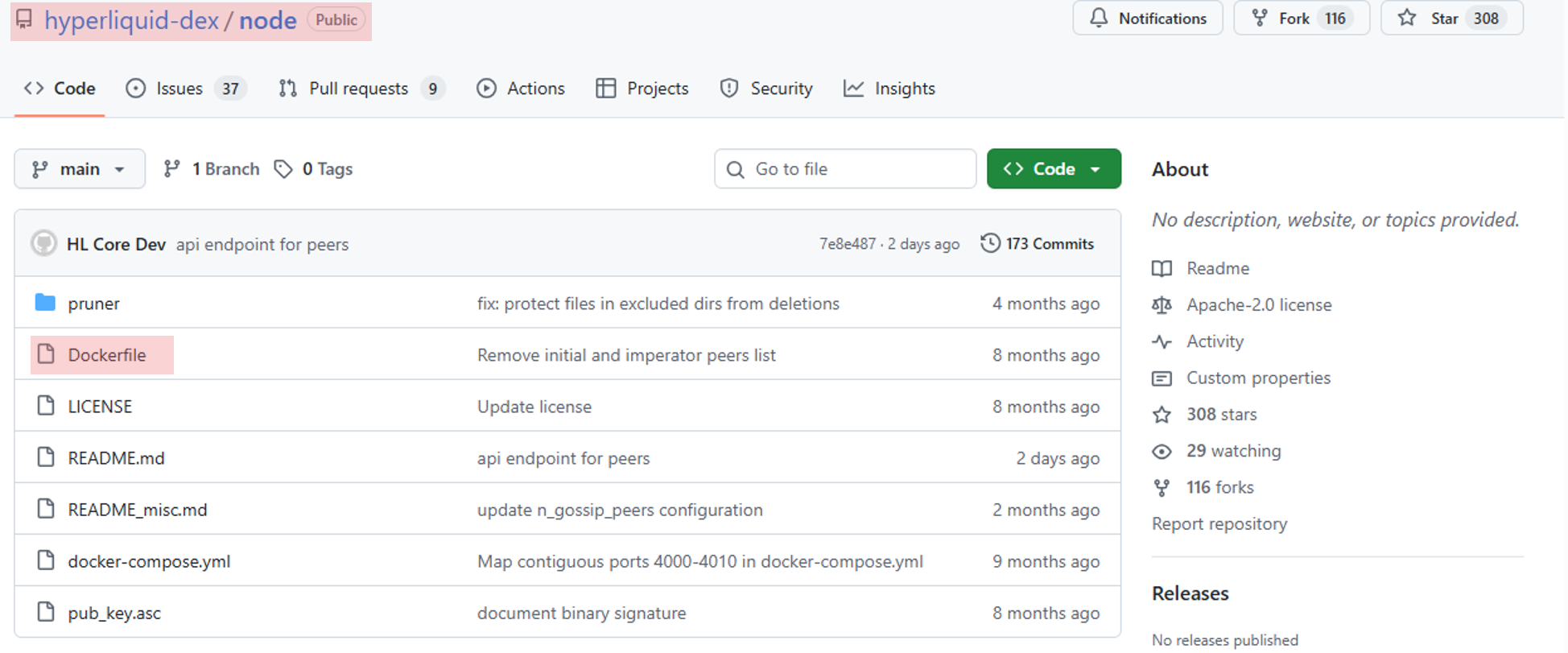
In an era where dependency vulnerabilities are rampant, running closed-source node software is like flying blindfolded. Validators must simply trust that the code contains no backdoors, hidden calls, or flawed logic – precisely the kind of faith-based setup Web3 was built to eliminate through a trustless architecture.
And Hyperliquid is not alone. LayerZero – once open source – closed its codebase after further funding rounds. The result? By September 2025, its market cap sits at just $467 million against $318 million raised – a marginal gain that hints at lost confidence.
Even Uniswap has moved away from pure openness, with Uniswap V4 adopting the Business Source License (BUSL) that “limits the use of the v4 source code in a commercial or production setting until June 15, 2027, at which point it will convert to a MIT license.”
This shift toward closed source does not just introduce risk. It undermines the very premise of Web3: validator sovereignty. If validators cannot see the code they run, we are not building a decentralized future; we’re recreating the black-box architectures of Web2 but with tokens.
Empowered Permissionless-ness
Open source is the natural companion to permissionless-ness. The two are inseparable, each reinforcing the other.
But why not simplify the codebase until anyone – even a 5-year-old – can run a validator? If the network is truly permissionless, shouldn’t everyone be able to participate, no matter their technical skill?
This sounds reasonable at first, but it’s a dangerous path. If the software is made so simple that validators do not need to understand what they are running, they are not empowered. They are simply reduced to passive operators. Handing them a Docker container and calling it “decentralized” might look like progress, but it is really just convenience disguised as participation. Plug in a machine, turn it on, and voilà – you’re a validator. No knowledge required.
Sounds good?
It’s not.
This is the opposite of what Web3 stands for. True permissionless-ness is not about making things easy. It is about making things possible for those willing to learn, verify, and contribute meaningfully. It is about enabling agency, not eliminating effort.
Permissionless-ness means everyone qualified has the right and the opportunity to participate.
I would not want a 5-year-old making foreign policy decisions without understanding diplomacy, just as I would not want him performing surgery without a medical degree. Granting access without competence is not inclusion – it is irresponsibility.
The goal isn’t to eliminate barriers entirely, but to lower them enough that anyone willing to become qualified can participate.
You might argue that politics already filters for qualifications – but you’d be wrong. Politics filters primarily for money and connections, not competence. It is a proof-of-stake system where those with capital or influence get elected, while truly capable outsiders remain excluded.
Web3 flips this entirely.
Here, if you’re qualified, you can participate. No financial gatekeeping, no inner circle required. Permissionless-ness does not mean everyone will become a validator; it means everyone can provided they put in the effort to understand the code, the tokenomics, and the responsibility.
Open-source acts as the gateway to this competence. It demands a “proof-of-work” of learning – not of wealth. It ensures that those maintaining the network actually understand it.
This is the essence of real decentralization:
Networks secured by capable operators, not convenient bystanders.
Web3 is built on self-reliance, and that self-reliance begins with open, verifiable code.
Own the Infrastructure
Web3’s ultimate promise is ownership. Not just of assets, but of the very infrastructure that powers the network. If you cannot verify, operate, or maintain the infrastructure yourself then you do not truly own anything. You are merely a guest in someone else’s system.
Imagine founding a city with your closest allies. You design its layout, raise its walls, distribute its land, and establish trade with neighboring settlements. But when invaders come, everyone must contribute to its defense.

Mastering combat is difficult. You must learn which swords hold an edge, which shields can stop arrows, where to position boiling oil. Skills that require time, effort, and dedication. There are no shortcuts in defense, because your enemy trains just as hard. If you arm untrained citizens and put them on the front lines, they won’t become heroes. They will become casualties, and risk the safety of everyone beside them.
Same with Web3.
An untrained validator is not just a risk to themselves. They are a risk to the entire network. We must strive for competence, not convenience. “Idiot-proof” systems do not attract geniuses; they attract idiots. The term idiot itself comes from the Greek idiōtēs – a private person who takes no part in public life of a polis or city-state. A network filled with such participants is not decentralized; it’s neglectful.
You could outsource your security. Hire mercenaries to defend your city or validators to run your nodes. But mercenaries follow profit, not principles. Without oversight, they may turn on you. The same is true in crypto: if you cannot audit the code you run, you are trusting strangers with your sovereignty.
This is why permissionless architecture paired with open-source code is so powerful. It allows those with the will to learn to also gain the means to participate without requiring extreme wealth, corporate affiliation, or institutional approval.
Running a validator node must become a fundamental skill of the digital age as essential as reading or writing. Because when it comes to money, sovereignty should not be optional. It becomes a prerequisite.
Open Source vs. Enterprise
To grasp the transformative potential of open-source systems in the new era of Web3, let’s place two iconic models:
- Decentralized, open-source Bitcoin network, and
- Centralized, enterprise-driven Apple
This comparison is meant to reveal meaningful patterns and not rigid rules, but the contrasts that emerge help illuminate why open-source models like Bitcoin represent such a foundational shift in how value is created and maintained in the digital age.
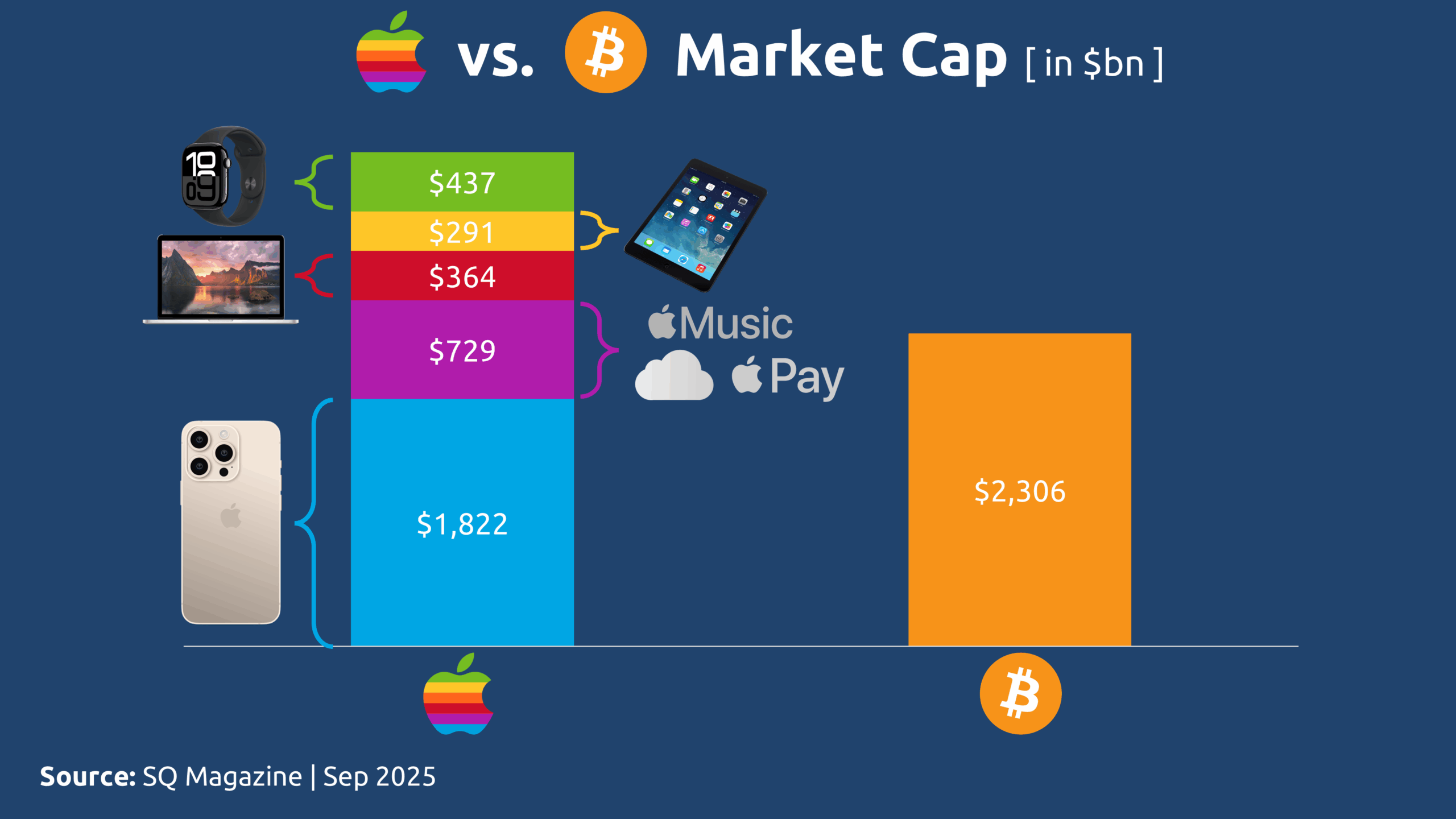
As of September 2025, Apple’s total market capitalization stands at approximately $3.6 trillion, while Bitcoin’s market cap reaches $2.3 trillion. Given that nearly 50% of Apple’s revenue is derived from iPhone sales, we can roughly attribute $1.8 trillion of its valuation specifically to the iPhone ecosystem. This places the iPhone’s implied market cap just below that of the entire Bitcoin network – a striking proximity given their fundamentally different models.
With this context established, we can delve deeper into the composition of value and participation within each system. Since 2008, cumulative downloads from the App Store have surpassed 400 billion applications.
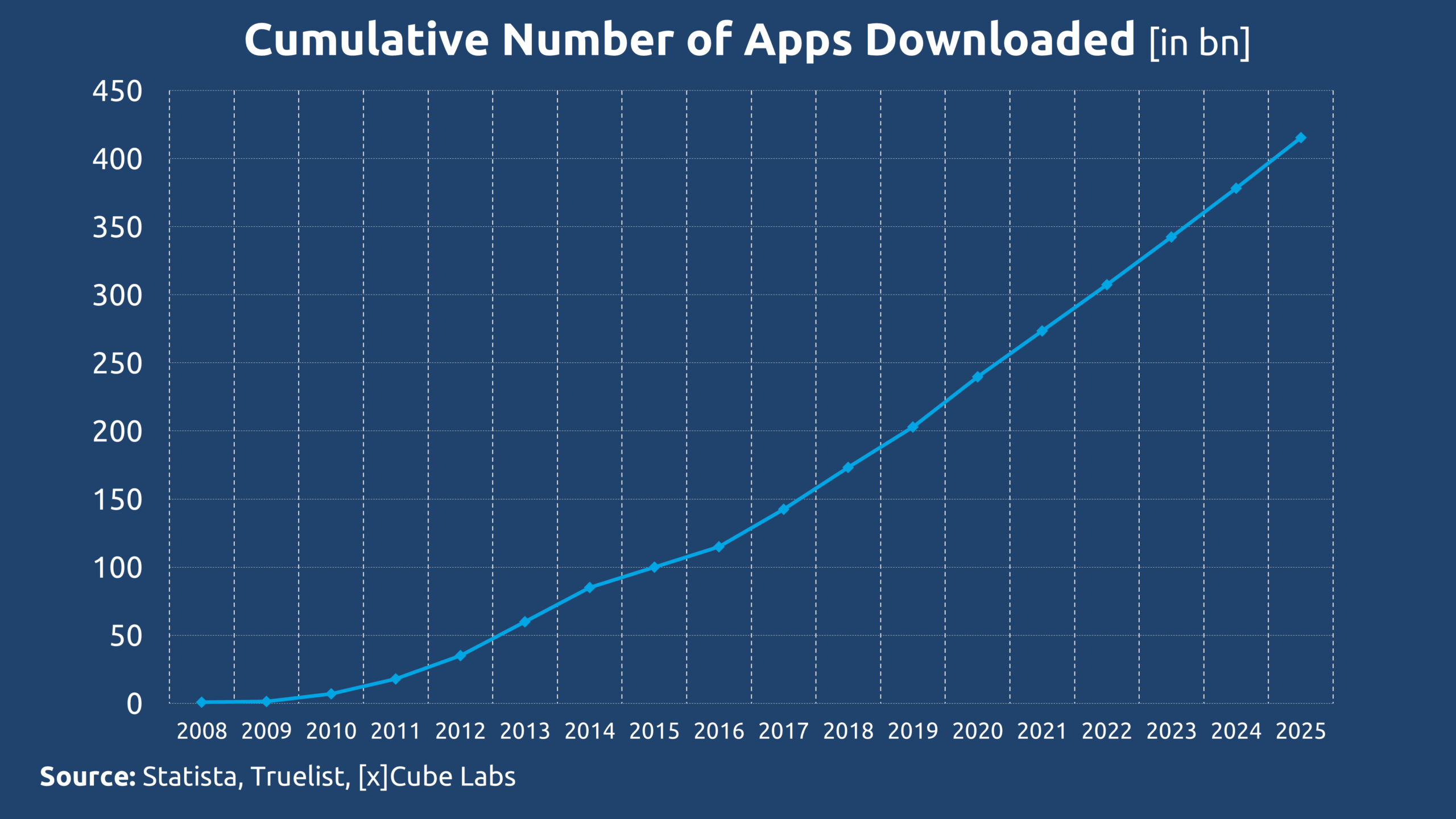
When compared to the more than 400 billion cumulative app downloads, the number of Bitcoin addresses holding any amount of BTC – approximately 57 million – seems modest at first glance. However, both metrics represent forms of user engagement, albeit of vastly different kinds.
It’s important to note that a single person may account for multiple app downloads, just as a single Bitcoin user may control multiple addresses. Many of these addresses hold negligible dust balances (e.g., ≤ 0.00001 BTC) left behind after transactions and effectively inactive.
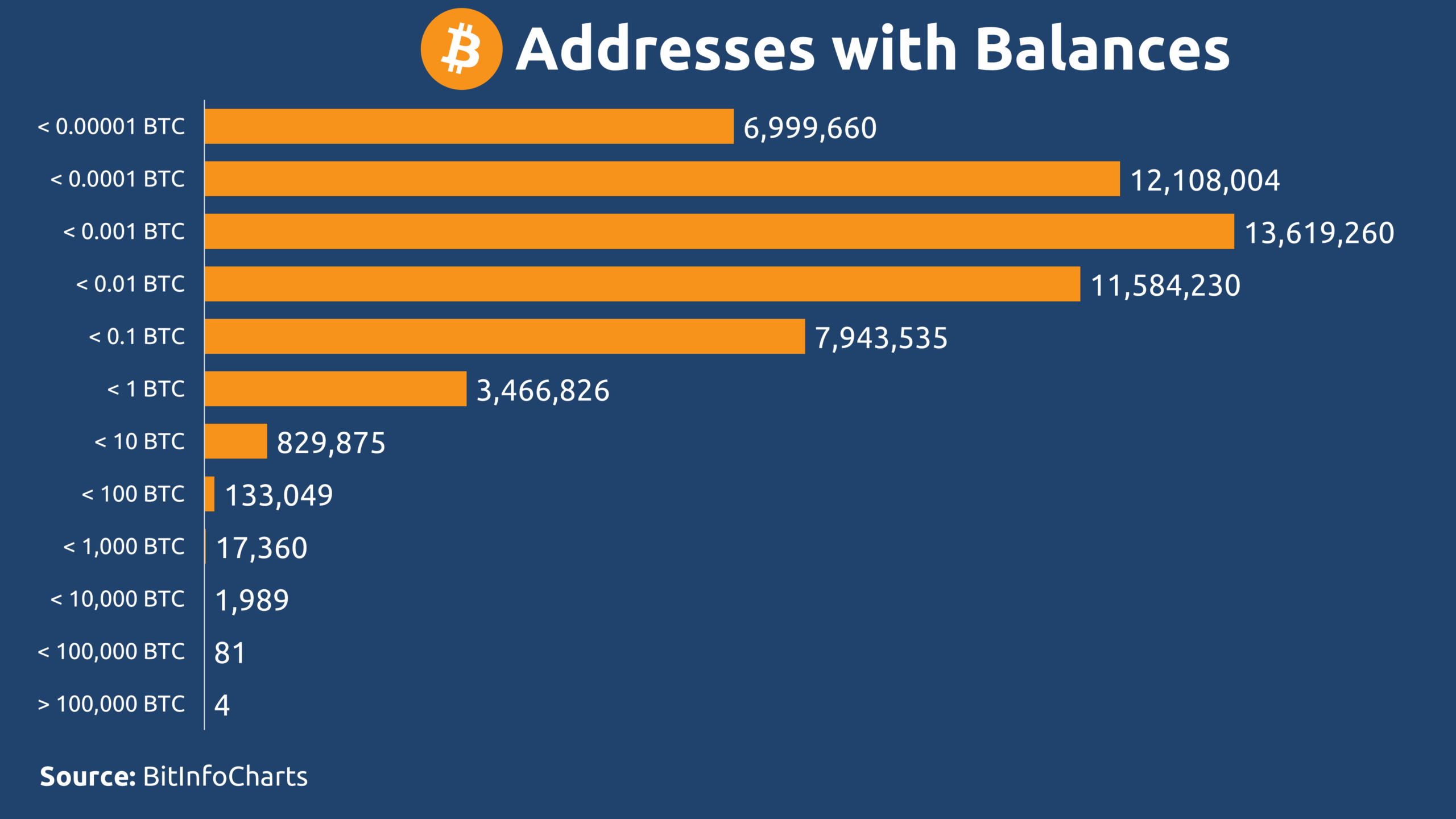
When adjusted for these factors, the two measurements become meaningfully comparable – not in absolute scale, but in their reflection of participation within each system. A single Bitcoin address can be seen as contributing economic value equivalent to approximately 7,326 app downloads. In other words, one meaningful action within an open-source, decentralized system holds weight comparable to over seven thousand actions in a centralized, Web2 enterprise model.
Let that sink in.
But what about those who maintain the infrastructure?
We can extend this comparison to the foundational supporters of each system. Since its launch, Apple has sold roughly 3 billion iPhone devices that act as passive conduits for its centralized services. In contrast, as of September 2025, there are nearly 24,000 Bitcoin nodes actively maintaining the network’s decentralized infrastructure.
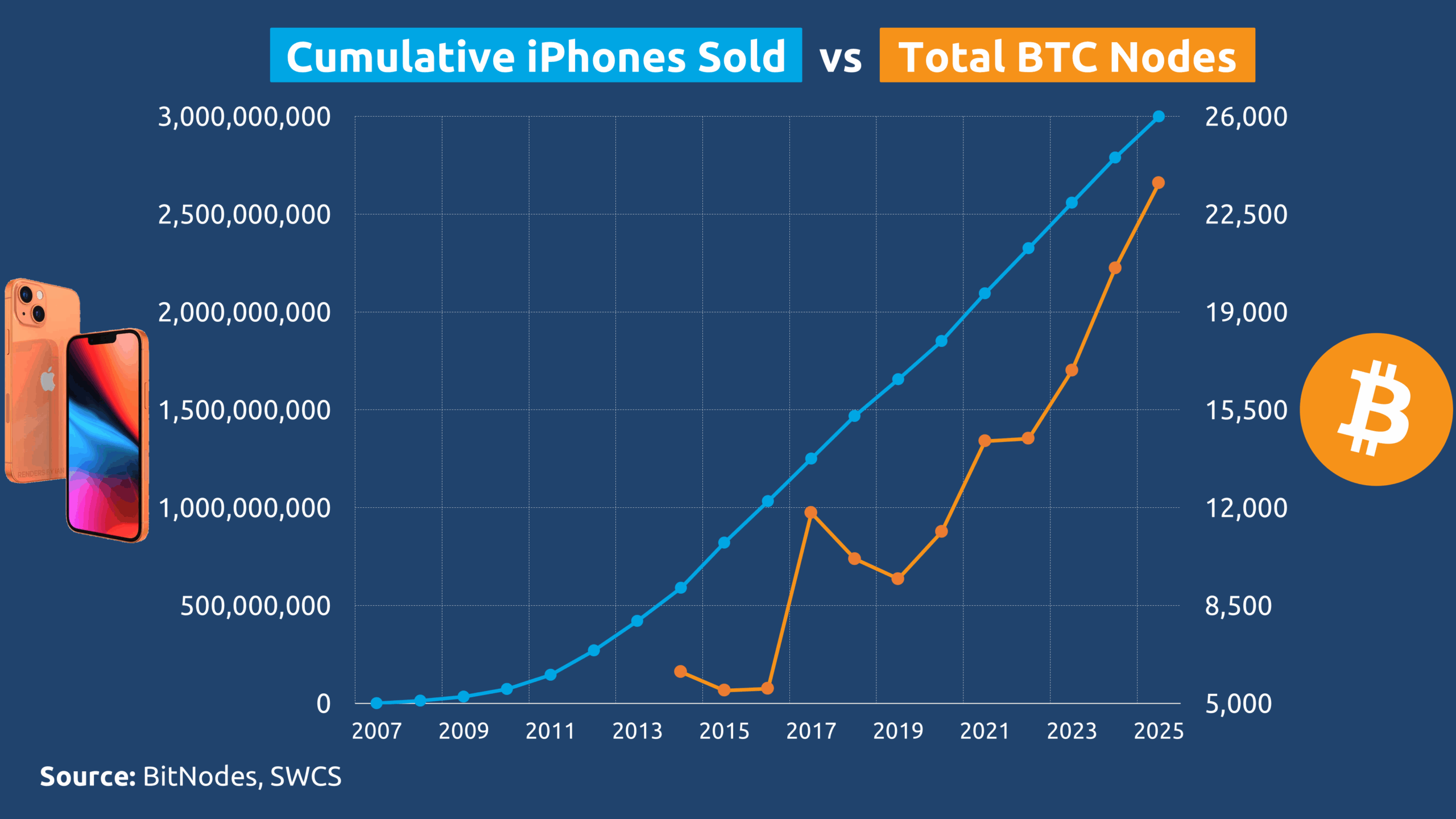
The value attribution per unit reveals a staggering divergence between the two models. Apple’s market capitalization per iPhone sold has declined to approximately $1,214, reflecting a depreciating trend since 2007 as market saturation and commoditization advance.
In sharp contrast, the market capitalization supported by each Bitcoin node serving as an active infrastructure maintainer rather than a passive consumer reaches nearly $100 million. This means every individual who runs a node contributes to sustaining a network value equivalent to that generated by 81,000 iPhones.
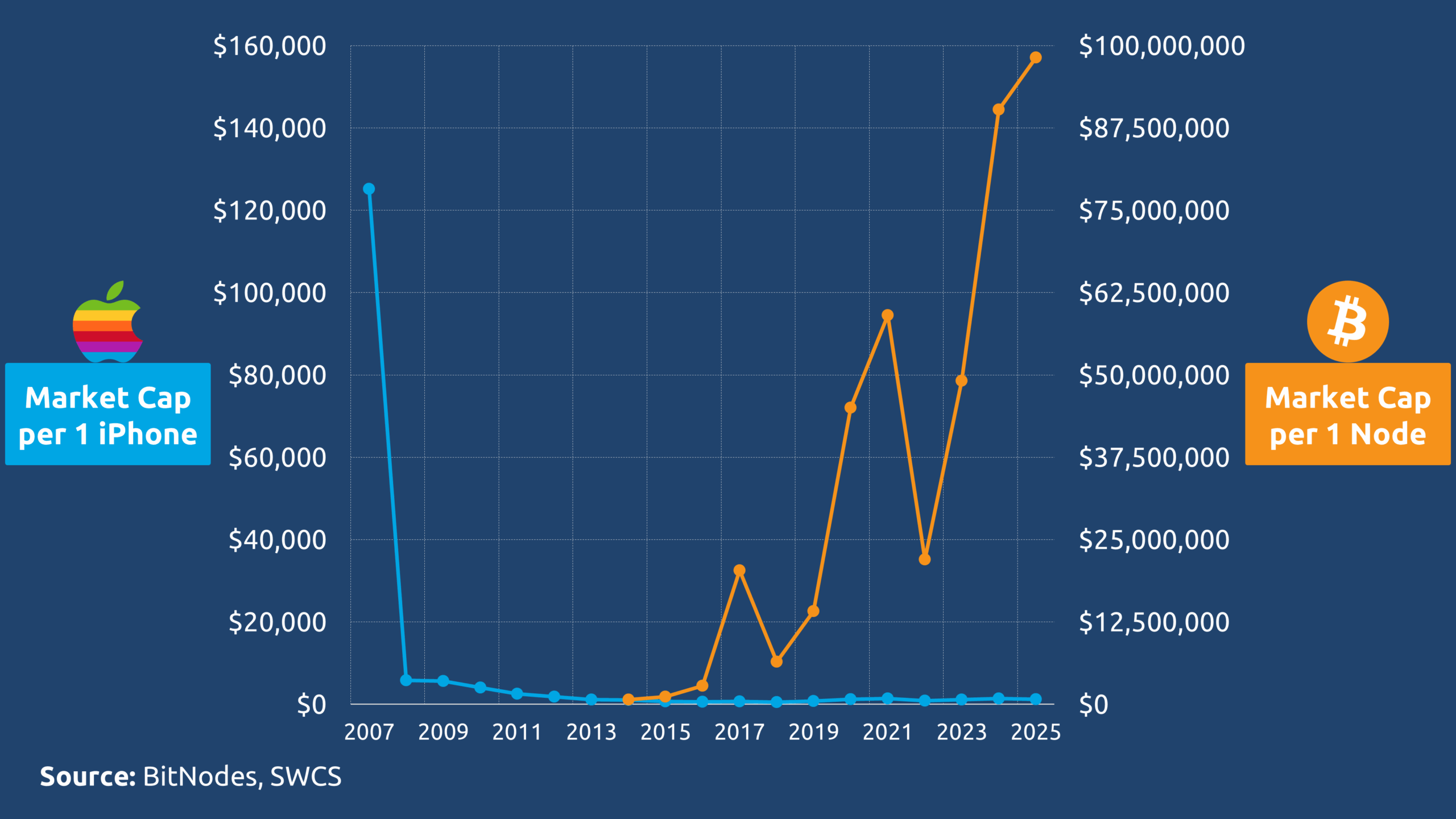
This is not just a difference in scale. This is a fundamental restructuring of how value is created and recognized in the digital age. Open-source, permissionless participation does not just compete with the enterprise model; it redefines the very meaning of contribution.